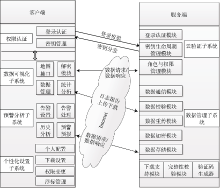
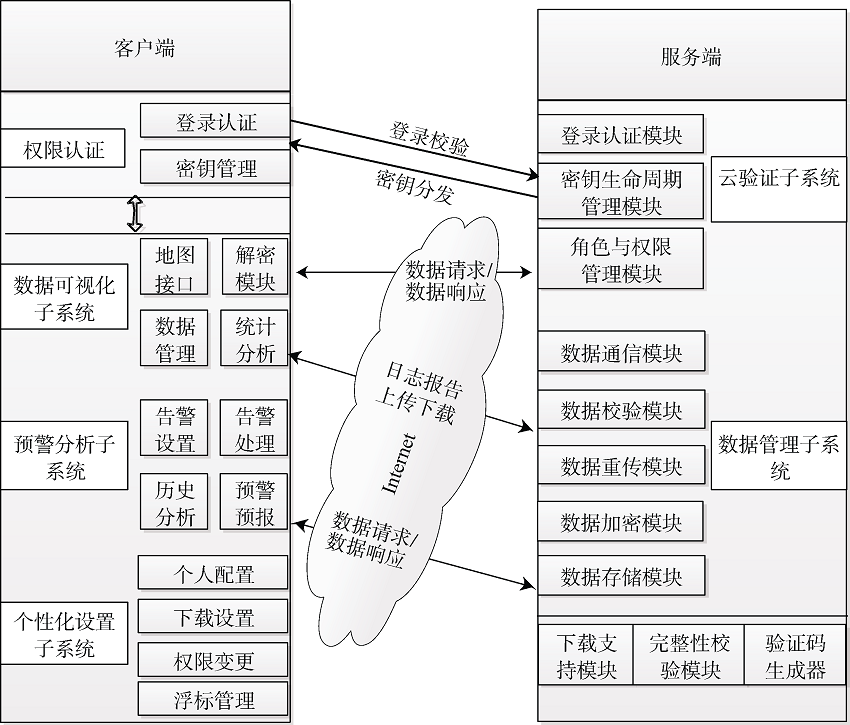
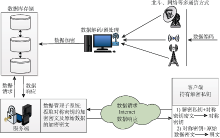
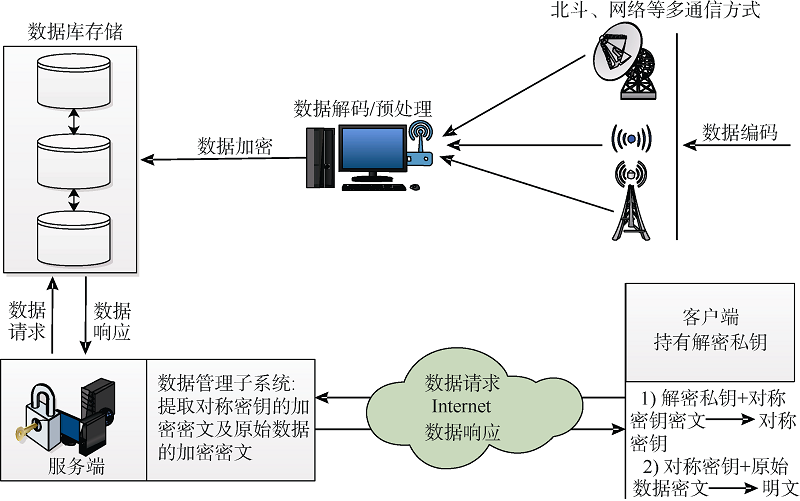
| [1] |
曹文熙, 孙兆华, 李彩, 等, 2018. 水质监测浮标数据采集和接收系统设计及其应用[J]. 热带海洋学报, 37(5):1-6.
|
|
CAO WENXI, SUN ZHAOHUA, LI CAI, et al, 2018. Design and application of data collecting system and data receiving system for water quality monitoring buoy[J]. Journal of Tropical Oceanography, 37(5):1-6 (in Chinese with English abstract).
|
| [2] |
何洪前, 李莎, 徐超, 2015. 基于云服务的南海海洋断面科学考察数据共享研究[J]. 热带海洋学报, 34(6):49-56.
doi: 10.11978/2015007
|
|
HE HONGQIAN, LI SHA, XU CHAO, 2015. Study on data sharing for scientific investigation in the South China Sea based on cloud computing[J]. Journal of Tropical Oceanography, 34(6):49-56 (in Chinese with English abstract).
doi: 10.11978/2015007
|
| [3] |
黄汉文, 2014. 海洋空间信息安全技术研究[J]. 航天电子对抗, 30(1):1-4.
|
|
HUANG HANWEN, 2014. Study on information security technology in ocean space[J]. Aerospace Electronic Warfare, 30(1):1-4 (in Chinese with English abstract).
|
| [4] |
刘长华, 冯立强, 贾思洋, 等, 2014. 信息技术在海洋观测浮标系统安全保障体系的应用[J]. 科研信息化技术与应用, 5(4):75-81.
|
|
LIU CHANGHUA, FENG LIQIANG, JIA SIYANG, et al, 2014. The application of information technology to security assurance of ocean observation buoy system[J]. E-Science Technology & Application, 5(4):75-81 (in Chinese with English abstract).
|
| [5] |
梅莉蓉, 2017. 海洋信息系统安全体系研究[J]. 通信技术, 50(8):1822-1825.
|
|
MEI LIRONG, 2017. Security architecture of marine information system[J]. Communications Technology, 50(8):1822-1825 (in Chinese with English abstract).
|
| [6] |
阮进勇, 徐凌宇, 丁广太, 2015. 数字海洋云计算平台工作流安全机制[J]. 计算机技术与发展, 25(1):155-158.
|
|
NGUYEN TIENDUNG, XU LINGYU, DING GUANGTAI, 2015. Security mechanism of workflow on cloud computing platform of Digital ocean[J]. Computer Technology and Development, 25(1):155-158 (in Chinese with English abstract).
|
| [7] |
辛冰, 符昱, 王漪, 等, 2018. 海洋科学数据共享平台设计与实现[J]. 海洋信息, 33(1):43-48, 55.
|
|
XIN BING, FU YU, WANG YI, et al, 2018. Design and implementation of marine science data sharing platform[J]. Marine Information, 33(1):43-48, 55 (in Chinese with English abstract).
|
| [8] |
FERRETTI L, PIERAZZI F, COLAJANNI M, et al, 2014. Scalable architecture for multi-user encrypted SQL operations on cloud database services[J]. IEEE Transactions on Cloud Computing, 2(4):448-458.
|
| [9] |
FUJISAKI E, OKAMOTO T, 2013. Secure integration of asymmetric and symmetric encryption schemes[J]. Journal of Cryptology, 26(1):80-101.
|
| [10] |
MA SHA, MU YI, SUSILO W, 2018. A generic scheme of plaintext-checkable database encryption[J]. Information Sciences, 429:88-101.
|
| [11] |
MARIAGE V, PELON J, BLOUZON F, et al, 2017. IAOOS microlidar-on-buoy development and first atmospheric observations obtained during 2014 and 2015 arctic drifts[J]. Optics Express, 25(4):A73-A84.
pmid: 28241666
|
| [12] |
RAGHAVENDRA S, GIRISH S, GEETA C M, et al, 2018. Split keyword fuzzy and synonym search over encrypted cloud data[J]. Multimedia Tools and Applications, 77(8):10135-10156.
|
| [13] |
WANG JUNCHENG, WANG ZHONGQIU, WANG YIMING, et al, 2016. Current situation and trend of marine data buoy and monitoring network technology of China[J]. Acta Oceanologica Sinica, 35(2):1-10.
|
| [14] |
ZHANG MINGHUA, HUANG DONGMEI, HE SHENGQI, et al, 2010. Construction of a platform for management of multi-dimension heterogeneous and mass ocean data[C]// International Conference on Electrical and Control Engineering. Wuhan, China: IEEE.
|
| [15] |
ZOU GUOLIANG, MA JINGJING, 2013. The data self-destruction technology research used in marine environmental monitoring buoy system[J]. Applied Mechanics and Materials, 336-338:2195-2198.
|
 ), LIU Yuqiang1,2(
), LIU Yuqiang1,2( ), LIU Tongmu1,2, LIN Guanying1,2, HUANG Hua1,2
), LIU Tongmu1,2, LIN Guanying1,2, HUANG Hua1,2